Our use case involves two AWS accounts but not via AWS OU ID because the account we provision the Grafana instance is NOT the root account, hence, we can’t enable Organization feature in IAM permission access settings.
Solution is to use IAM assumable role. Our prod account will have the Grafana instance running, and we want to ingest Cloudwatch and X-Ray data from dev.
Terraform
PROD
We use AWS_SSO at work, so thats what we will go with for authentication_providers.
locals {
stage = "prod"
dev_grafana_role_arn = "arn:aws:iam::{ dev_aws_id }:role/dev-grafana-cross-account-access"
}
module "managed_grafana" {
source = "terraform-aws-modules/managed-service-grafana/aws"
version = "~> 1.8"
name = "${local.stage}-grafana"
description = "Managed by Terraform"
use_iam_role_name_prefix = false
account_access_type = "CURRENT_ACCOUNT"
authentication_providers = ["AWS_SSO"]
permission_type = "SERVICE_MANAGED"
data_sources = ["CLOUDWATCH", "XRAY"]
notification_destinations = ["SNS"]
associate_license = false
}
# This policy is used by AWS managed grafana to assume the cross-region role from dev account.
data "aws_iam_policy_document" "managed_grafana" {
version = "2012-10-17"
statement {
effect = "Allow"
actions = ["sts:AssumeRole"]
resources = [local.dev_grafana_role_arn]
}
}
resource "aws_iam_role_policy" "managed_grafana" {
name = "${local.stage}-grafana-cross-region-access-policy"
policy = data.aws_iam_policy_document.managed_grafana.json
role = module.managed_grafana.workspace_iam_role_name
}
DEV
locals {
stage = "dev"
prod_grafana_role_arn = "arn:aws:iam::{ prod_aws_id }:role/prod-grafana"
}
# This role is used by AWS managed grafana from the prod account.
module "managed_grafana_assumable_role" {
source = "terraform-aws-modules/iam/aws//modules/iam-assumable-role"
version = "5.4.0"
trusted_role_arns = [local.prod_grafana_role_arn]
trusted_role_services = ["grafana.amazonaws.com"]
create_role = true
role_name = "${local.stage}-grafana-cross-account-access"
role_requires_mfa = false
custom_role_policy_arns = [
"arn:aws:iam::aws:policy/AWSXrayReadOnlyAccess",
"arn:aws:iam::aws:policy/CloudWatchReadOnlyAccess",
]
number_of_custom_role_policy_arns = 2
}
Grafana Dashboard Setup
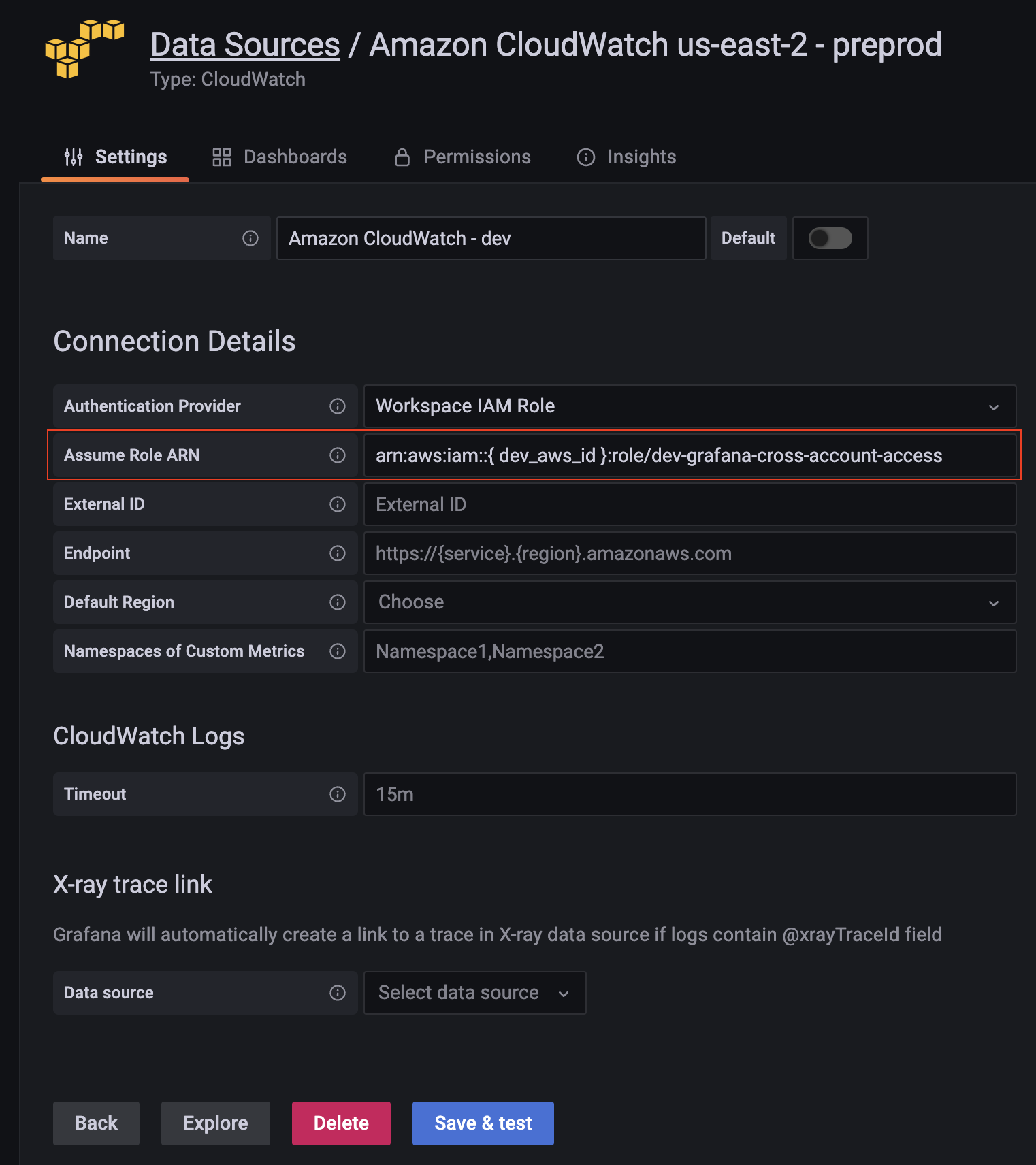
When adding a new data source from the dev account, simply edit the Assume Role ARN and enter the one we created in dev.
arn:aws:iam::{ dev_aws_id }:role/dev-grafana-cross-account-access